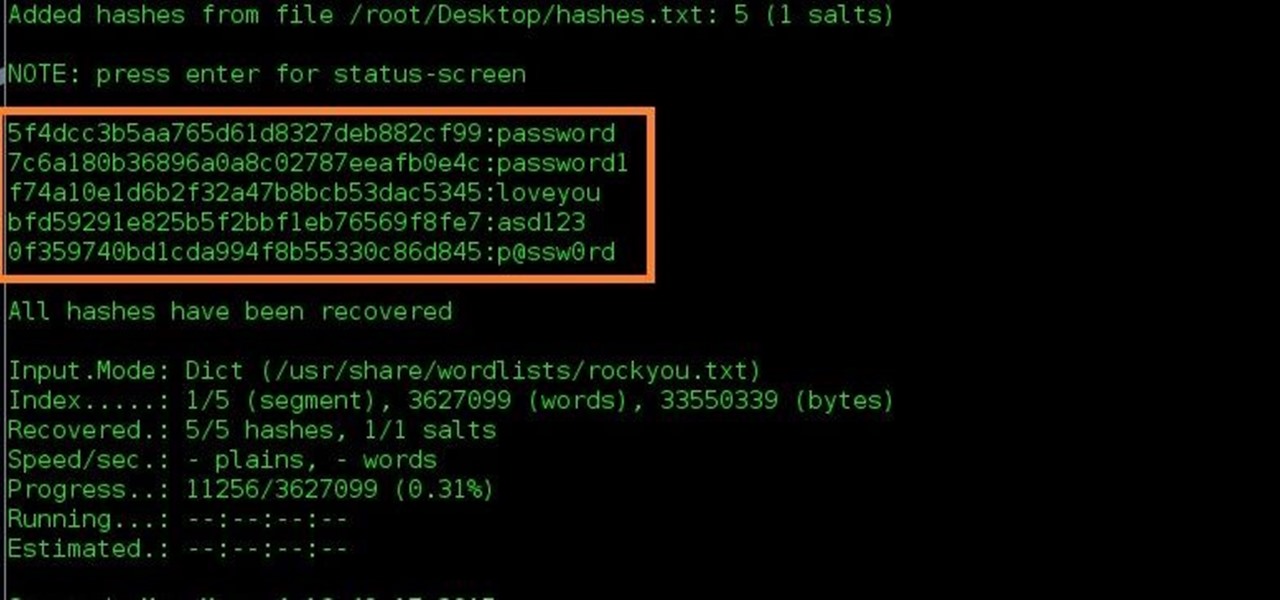
John The Ripper Crack Sha1 Hash Value
We have prepared a list of the top 10 best password cracking tools that are widely used by ethical hackers and cybersecurity experts. These tools include the likes of Aircrack, John the Ripper. (2) Wordlist Mode. In this mode, John is using a wordlist to hash each word and compare the hash with the password hash. If you do not indicate a wordlist, John will use the one it comes bundled with which has about 3,500 words which are the most common passwords seen in password dumps. John the Ripper cracked exactly 122.717.140 hashes, which is about 63.92% of the total file. I guess you could go higher than this rate if you use the rules in John the Ripper. If you want to try your own wordlist against my hashdump file, you can download it on this page.
When beginning tom without the -format parameter, hash type detection reports broken hash varieties.For example when attempting to crack á md5 hash invalid information is definitely printed. dynamic=md5($g) can be not a legitimate hash type. I'm affraid I was unable to discover your point. Therefore, I attempted JtR (the packed edition). Everything is definitely working fine. I would expect that the file format 'dynamic=md5($g)' will be listed when working the right after command word./david -listing=formats grep 'dynamic='But that's not really the situation.The 2nd issue is certainly that the hash 527bn5b5d689e2c32ae974c6229ff785 can be recognized as a possible SHA1 hash.is usually acknowledged as a achievable SHA1It could become Ráw-SHA1-AxCrypt (If l'michael not wrong). Neither Ráw-SHA1-ng, nór has160.
$ john-the-ripper MD5.hash -format=Raw-SHA1-ngUsing default input coding: UTF-8No security password hashes packed (observe Common questions)$ john-the-rippér MD5.hash -fórmat=Ráw-SHA1-AxcryptUsing default input encoding: UTF-8Loaded 1 security password hash (Ráw-SHA1-AxCrypt SHA1 128/128 SSE2 4x)Press 'queen' or CtrI-C to abórt, almost any other key for standing0g 0:00:00:03 3/3 0g/beds 2282Kg/s 2282Kd/s 2282KD/s 0r5988.0r5984Session aborted. /crack-license-file-autocad-2002-torent.html.
John The Ripper Crack Sha1 Hash Value 2
John The Ripper Hash Formats. John the Ripper is a favourite password cracking tool of many pentesters. There is plenty of documentation about its command line options. I’ve encountered the following problems using John the Ripper. These are not problems with the tool itself, but inherent problems with pentesting and password cracking in.
John-users - Re: Making use of John for cracking solitary hashesDate: Sunlight, 9 April 2006 03:10:38 +0300From: Ali Polatel Tó: john-usérs@.ts.openwall.comSubjéct: Re: Making use of John for cracking solitary hashesThanks a number.It works right now.What are usually the avaliable formats that I can make use of?
I have a collection of password hashes. Mainly because considerably as I understand the -rules option only enables you to define rules for the password the consumer may be making use of (foobar, foobar123, y00bar).-format corresponds to the format of the hash: there are many predefined rules , so you can alter your file to the fórmat salt:md5(saIt+password), eg: 9e7443:7e97ff201ff38416138a22a7f3adfa3b9d10e947481bd94b16eed7df6b6e2806, and find a format which functions username:md5(usérname+password) for example.Another choice would become to use powerful scripts.
John The Ripper Crack Sha1 Hash Value 1
This method will be more difficult but furthermore more versatile.