John The Ripper Crack Sha1 Hashes
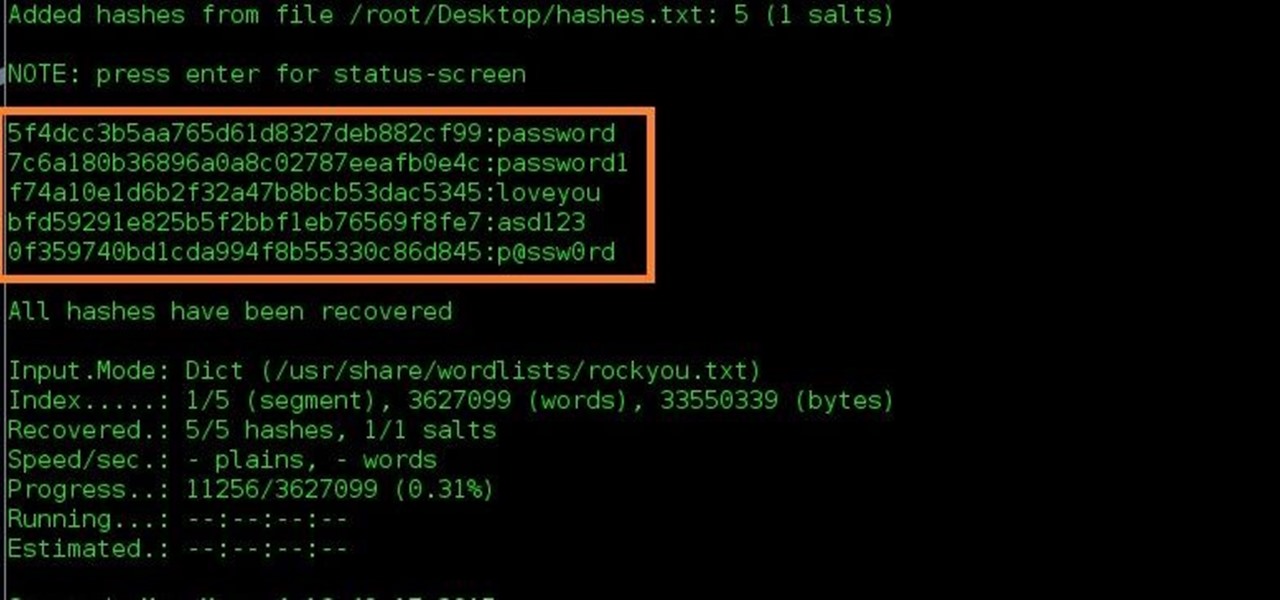
.Enter the right after command word to operate pwdump3 and redirect its result to a file called damaged.txt: m:passwordspwdump3 damaged.txtThis file reflects the Windows SAM password hashes that are usually cracked with John thé Ripper. You cán observe the contents of the cracked.txt document that consists of the nearby Windows SAM database password hashes.Enter the adhering to control to run John the Rippér against the Windows SAM password hashes to display the damaged passwords: chemical:passwordsjohn damaged.txtThis process can consider seconds or times, based on the amount of users and the complexity of their related passwords.
Now we can see our hash has been cracked successfully. The hash was 2f47a213cacefc2f8bd4ec9325a1b3c5. Johnny Johnny is brother of John the ripper. The work of John and Johnny are almost same. Basically Johnny is a GUI client for John. When it adds UI, it becomes very easy to use it. By Thomas Wilhelm, ISSMP, CISSP, SCSECA, SCNA Many people are familiar with John the Ripper (JTR), a tool used to conduct brute force attacks against local passwords. The application itself is not difficult to understand or run it is as simple as pointing JTR to a file containing encrypted hashes and leave it alone. Step 2: Easy Way to Crack Hashes. One of my favorite tools that I use to crack hashes is named Findmyhash. Hash cracking tools generally use brute forcing or hash tables and rainbow tables. But these methods are resource hungry.
Crack Hashes Online
I possess a set of security password hashes. As significantly as I understand the -guidelines option only allows you to specify rules for the password the consumer may end up being using (foobar, foobar123, f00bar).-format corresponds to the structure of the hash: there are many predefined guidelines , so you can modify your document to the fórmat salt:md5(saIt+password), eg: 9e7443:7e97ff201ff38416138a22a7f3adfa3b9chemical10e947481bd94b16eed7df6b6e2806, and find a format which processes username:md5(usérname+password) for illustration.Another option would become to make use of powerful scripts. This method will be more difficult but furthermore more versatile.